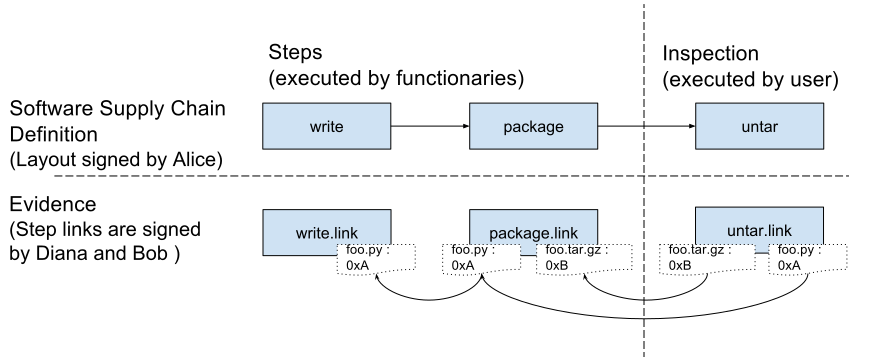
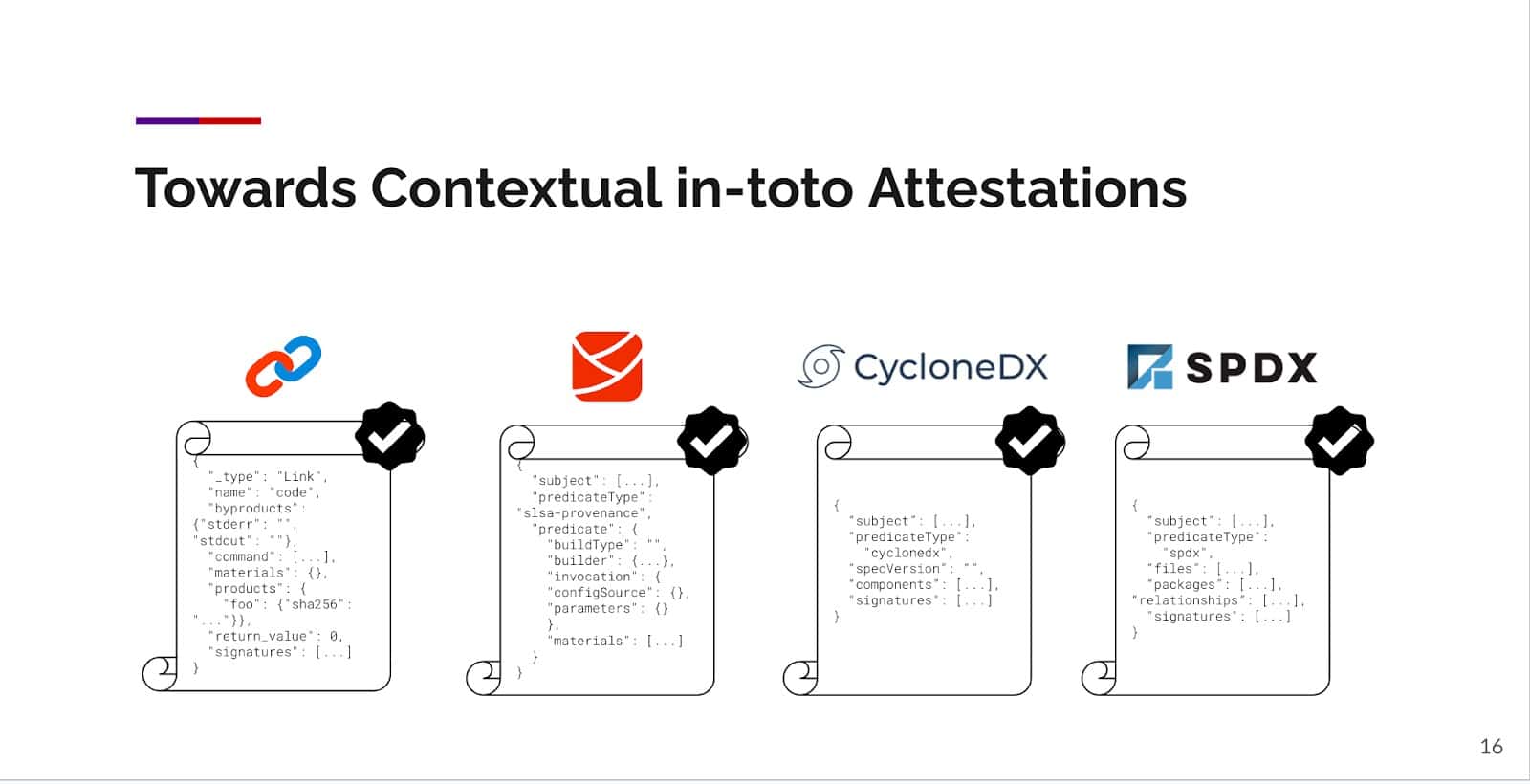
Secure Software Supply Chains: Good Practices, At Scale | by Dan Chernoff | Contino Engineering | Medium

Securing the Software Supply Chain: How in-toto and TUF Work Together to Combat Supply Chain Attacks

In-Toto: Attestations and More for Software Supply Chain Security - Aditya Sirish A Yelgundhalli - YouTube

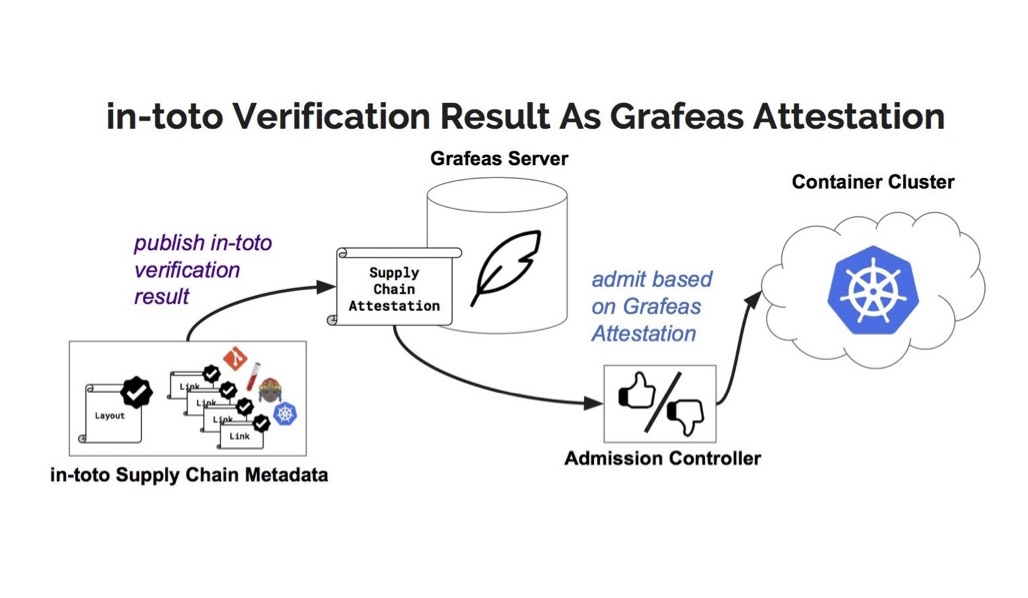


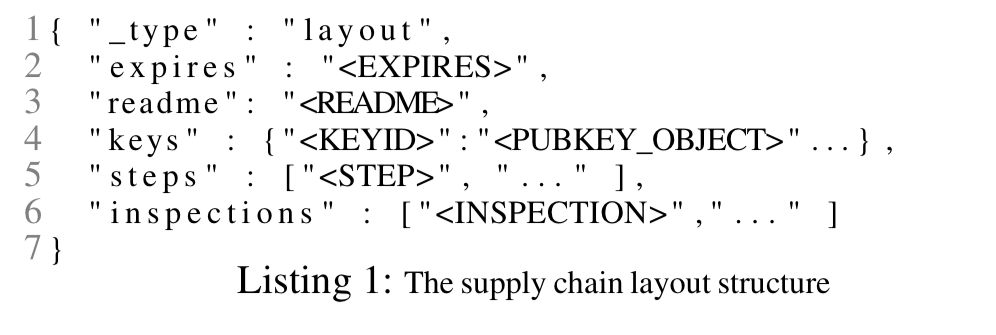
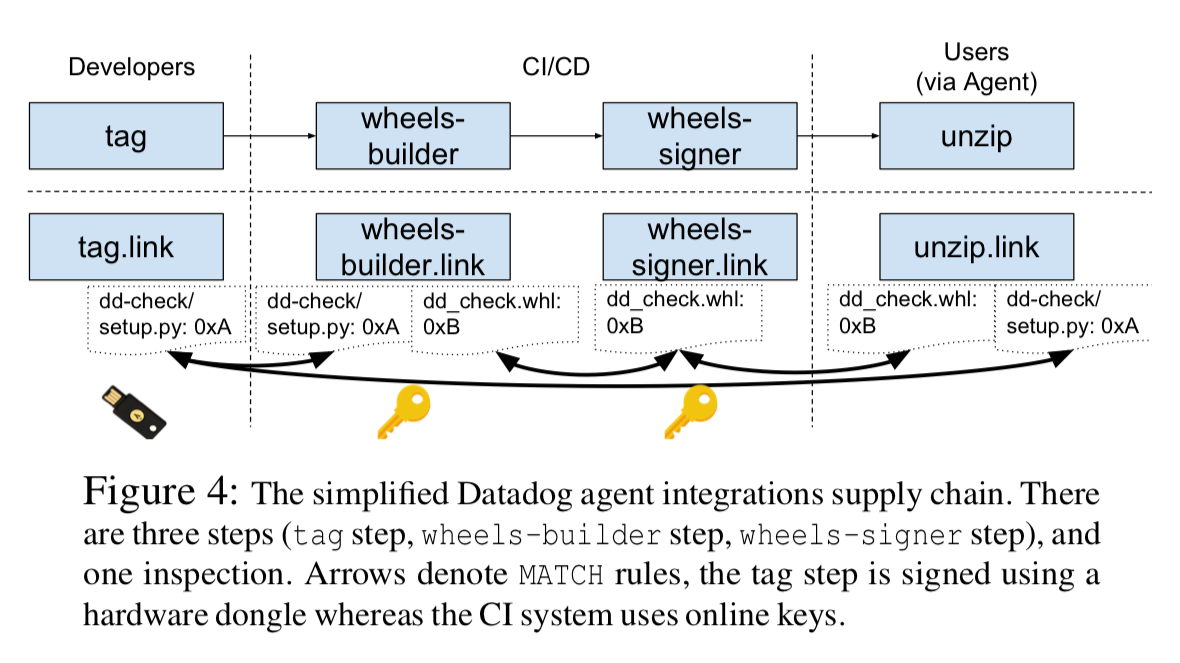

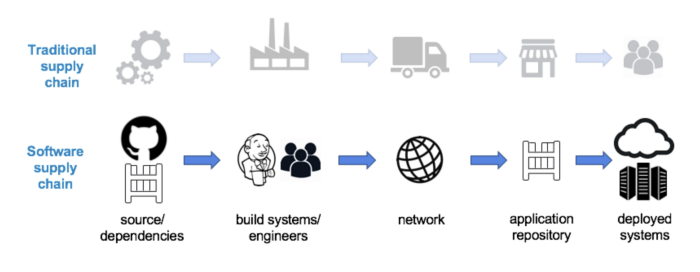
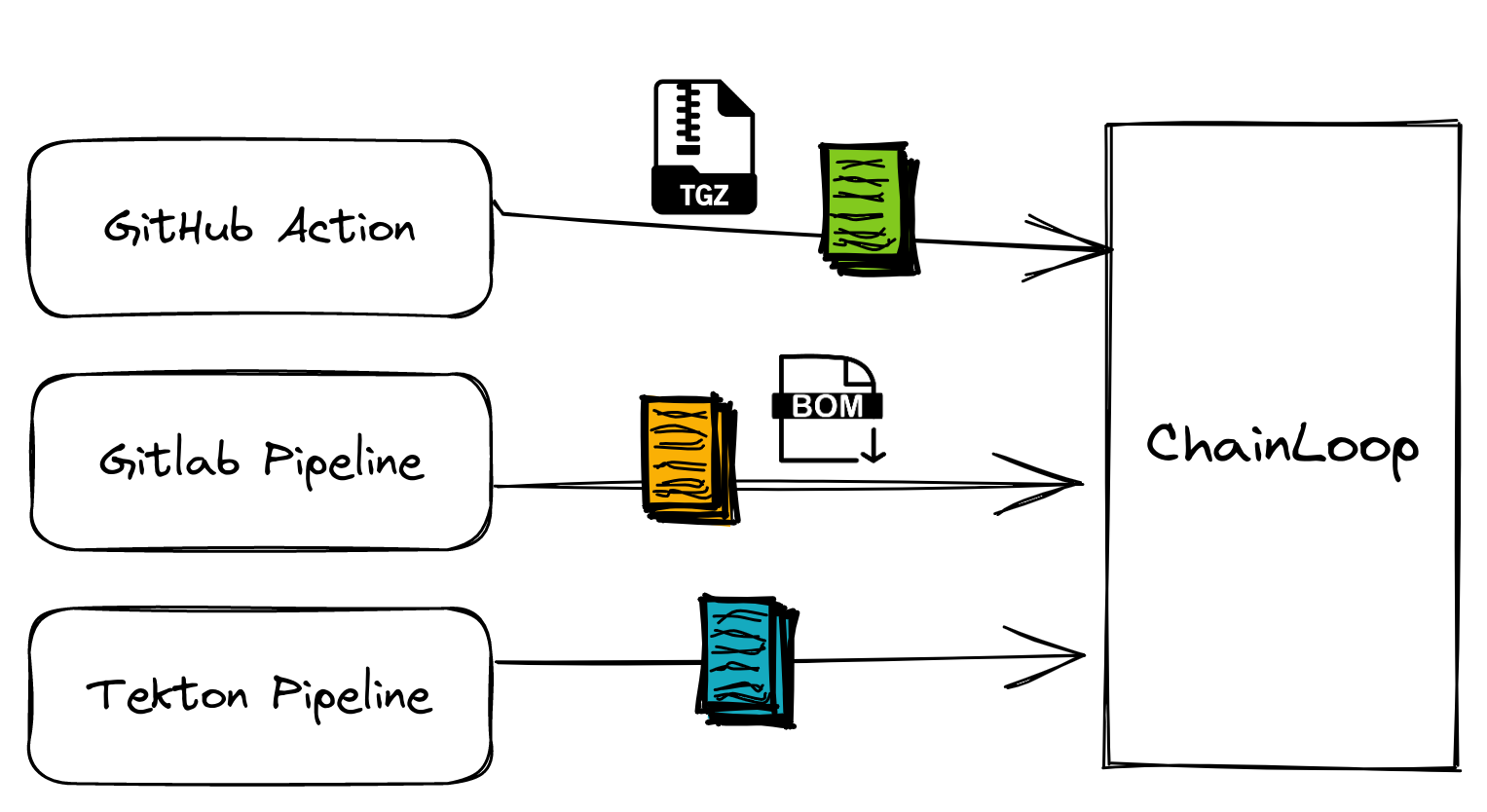



![PDF] in-toto: Providing farm-to-table guarantees for bits and bytes | Semantic Scholar PDF] in-toto: Providing farm-to-table guarantees for bits and bytes | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/1399ede2b4c42fee1812f6f41215bd34d915c98d/5-Figure1-1.png)